For an upcoming project and blog article, I’m going to need a Linux setup on my main machine. The project requires me to use a minimal install of CentOS 7 (Linux) as the operating system. In order to run another operating system on my hardware I will use VirtualBox so […]
Discourse is an open source forum software developed by Jeff Atwood, the co-founder of Stack Overflow. The application is written with Ruby on Rails. As a product designed for the next decade of the Internet, Discourse breaks with existing forum software by its commitment to open source, concise page style […]
ent a beneficial tool for bug bounty hunters which is specially designed to check the security of any web application. OWASP ZAP is an open-source web application security scanner. It is intended to be used by both those new to application security as well as professional penetration testers. It has […]
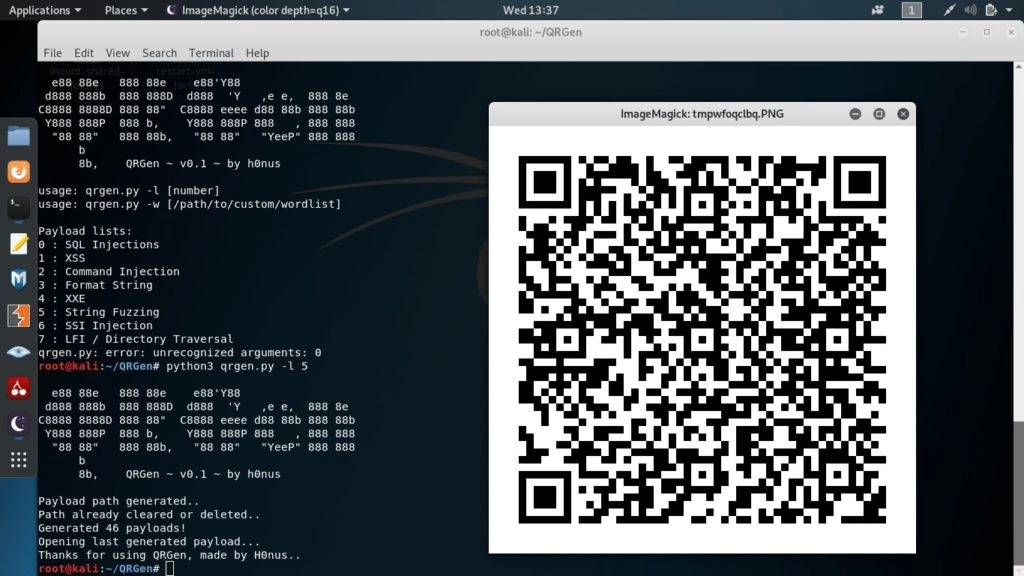
Hey Folks, in this article we will show you the whole scenario that how attackers hack android smartphone by using QR code and HTA attack techniques. To accomplish this task we must have a Kali Linux operating system. We think most people are familiar with QR code, so we only […]
AdvPhishing is a phishing tool which allows the user to access accounts on social media even if two-factor authentication is activated. AdvPhishing allows the user to gain the target’s username, password and latest one-time password (OTP) in real-time as the target is logging in. In addition to this the user […]
Hey Folks, we are excited to write this masterpiece article on DNS enumeration tool which can help you to find some subdomain takeover vulnerability in different website as well as bounty. Dnsenum is a tool for DNS enumeration, which is the process of locating all DNS servers and DNS entries for […]
Like any other operating system, GNU/Linux has implemented a memory management efficiently and even more than that. But if any process is eating away your memory and you want to clear it, Linux provides a way to flush or clear ram cache. How to Clear Cache in Linux? Every Linux […]
Along with half of the world’s population, I find myself working from home due to sheltering requirements imposed on us by the COVID-19 pandemic. In these troubled times, communication with my friends and family have become critical. I found that I needed ways to stay in touch with them easily. […]
Remove any the previous installation of Apache if it is installed from yum command in the target system. Installation procedure To proceed with the installation procedure, run the below command which installs all the required packages for the source code compilation of Apache and press y to continue with the installation. [root@linuxtips ~]# yum […]
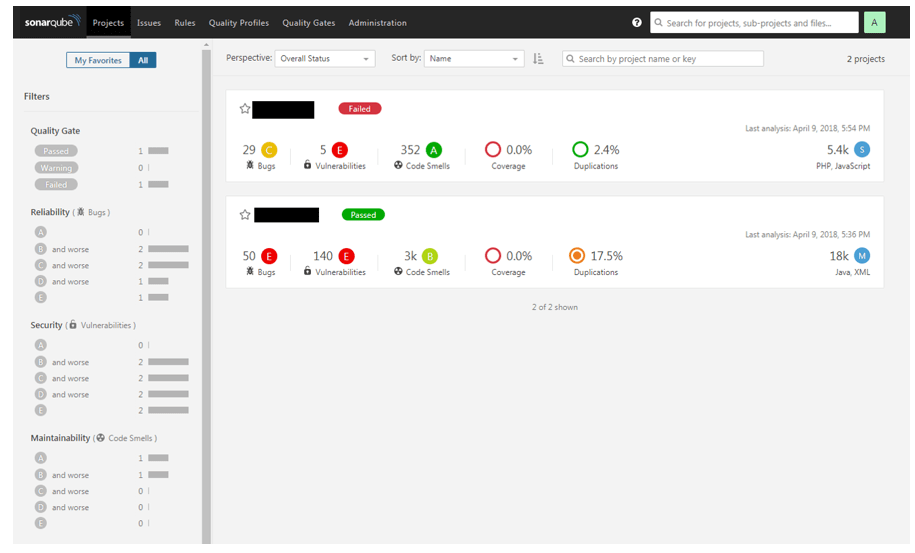
It has been sometime since I’ve seen an updated SonarQube tutorial here on DZone, so I thought that I would go through a jump start guide for you. I’m assuming that you are working in one of the common Linux distros (most of this tutorial works as well for Windows, […]