
What is tor browser ?
Tor began its life in the 1990s when researchers at the US Naval Research Laboratory developed “onion routing.” Onion routing makes it possible to pass messages through a network anonymously. It uses multiple layers of encryption that get peeled off one by one (like peeling an onion) as the message passes through multiple nodes in the network.
In 2004, the Navy released the second generation of Tor. In 2006, researchers involved in Tor incorporated the Tor Project and took responsibility for maintaining Tor.
If you’re investigating a competitor, researching an opposing litigant in a legal dispute, or just think it’s creepy for your ISP or the government to know what websites you visit, then the Tor Browser might be the right solution for you.
A few caveats: Browsing the web over Tor is slower than the clearnet, and some major web services block Tor users. Tor Browser is also illegal in authoritarian regimes that want to prevent citizens from reading, publishing, and communicating anonymously. Journalists and dissidents around the world have embraced Tor as a cornerstone of democracy online today, and researchers are hard at work improving Tor’s anonymity properties.
Where to download Tor Browser
Tor Browser is available for Linux, Mac, and Windows, and has also been ported to mobile. You can download desktop versions from the Tor Project website. If you’re on Android, find OrBot or OrFox on the Google Play Store or F-Droid. iOS users can grab OnionBrowser from the Apple App Store.
How to use the Tor Browser on mobile and cell phones
More and more people are browsing the web from their phones, and in poorer parts of the world that are mobile first, people are browsing the web only from their phones. As a result, the Tor Project has spent a couple years working to build a better Tor Browser for mobile phone users.
In September 2019, the Tor Project announced the official release of Tor Browser for Android, replacing the Guardian Project’s Orfox as the officially endorsed Tor Browser for Android. (The Guardian Project’s similarly named Orbot, a Tor proxy for Android that lets you tunnel all your app traffic over Tor, not just web traffic, continues to be alive and well.)
Due to technical restrictions on Apple’s proprietary iOS platform, the Tor Project has not yet released an official Tor Browser for iPhone and iPad users but endorses OnionBrowser for iOS users who want to browse the web anonymously. Major security improvements are in the pipeline for OnionBrowser, including fixing some information leakage issues and enabling per-website security parameters. The latest and greatest version of OnionBrowser should be out by early November 2019, the developers tell CSO.
How Tor Browser works
Tor Browser routes all your web traffic through the Tor network, anonymizing it. As the images below illustrate, Tor consists of a three-layer proxy, like layers of an onion (hence Tor’s onion logo). Tor Browser connects at random to one of the publicly listed entry nodes, bounces that traffic through a randomly selected middle relay, and finally spits out your traffic through the third and final exit node.
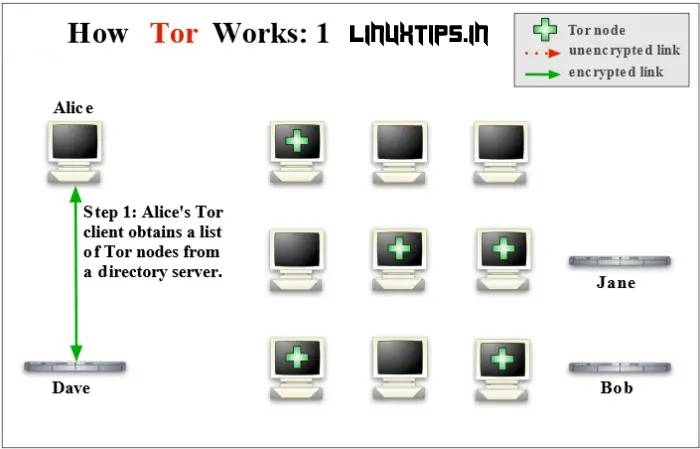
As a result, don’t be surprised if Google or another service greets you in a foreign tongue. These services look at your IP address and guesstimate your country and language, but when using Tor, you will often appear to be in a physical location halfway around the world.
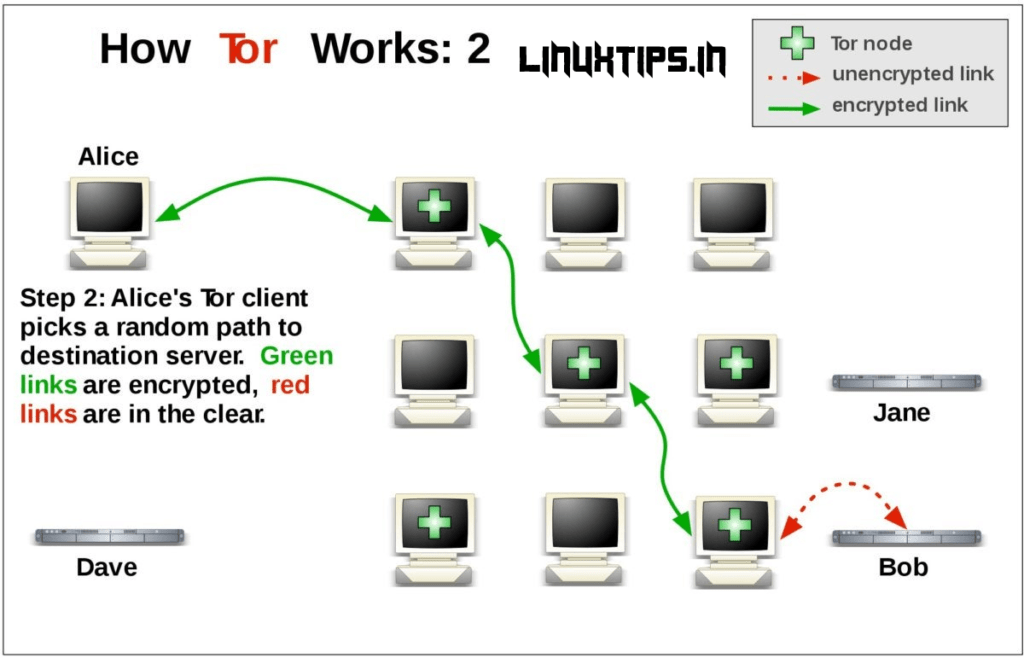
If you live in a regime that blocks Tor or need to access a web service that blocks Tor, you can also configure Tor Browser to use bridges. Unlike Tor’s entry and exit nodes, bridge IP addresses are not publicly listed, making it difficult for web services, or governments, to blacklist those IP addresses.
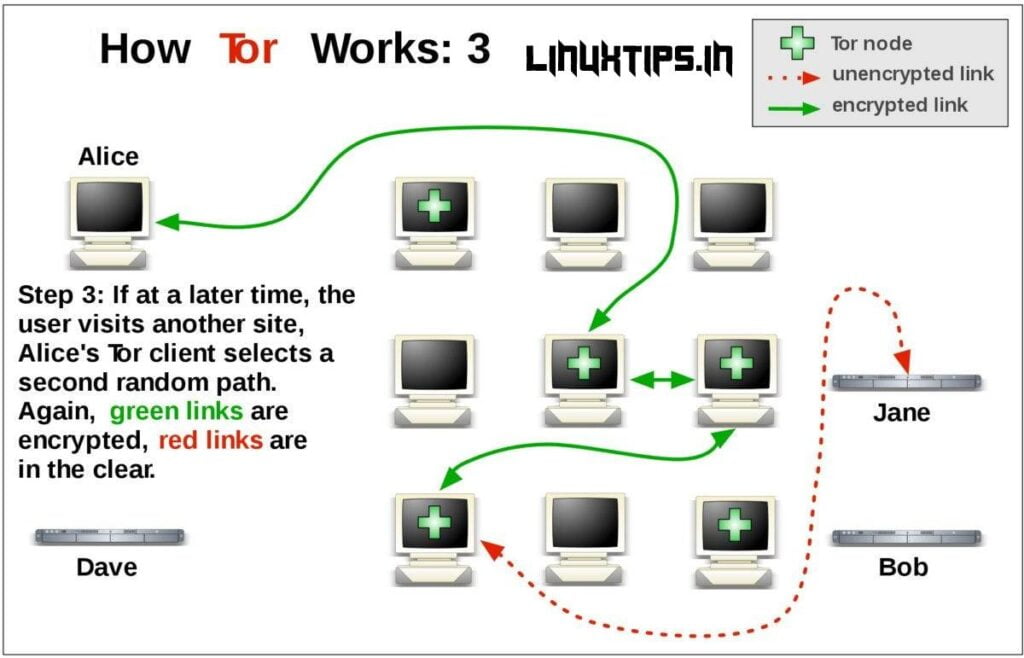
The Tor network routes TCP traffic of all kinds but is optimized for web browsing. Tor does not support UDP, so don’t try to torrent free software ISOs, as it won’t work.
How to get on the dark web?
Let’s get this “dark web” nonsense out of the way once and for all. While it’s true that some criminals use Tor to commit crimes, criminals also use the regular internet to commit crimes. Bank robbers use getaway cars on public highways to commit crimes. We don’t slander highways or the internet, because that would be foolish. Tor has tons of legitimate uses and is considered by many a cornerstone of democracy today.
So when you hear people talking in scared whispers about the “dark web” or the “deep web” or somesuch nonsense, understand that there is a lot more going on here than just “The Four Horsemen of the Infocalypse are using computers in non-normative ways.” Anonymity online is not merely the bailiwick of criminals and trolls.
As a practical matter, Tor is for ordinary people, because criminals willing to break the law can achieve better anonymity than Tor provides. As the Tor FAQ points out:
Doesn’t Tor enable criminals to do bad things?
Criminals can already do bad things. Since they’re willing to break laws, they already have lots of options available that provide better privacy than Tor provides. They can steal cell phones, use them, and throw them in a ditch; they can crack into computers in Korea or Brazil and use them to launch abusive activities; they can use spyware, viruses, and other techniques to take control of literally millions of Windows machines around the world.
Tor aims to provide protection for ordinary people who want to follow the law. Only criminals have privacy right now, and we need to fix that.
Is Tor Browser anonymous?
Tor Browser offers the best anonymous web browsing available today, but that anonymity is not perfect. We are currently witnessing an arms race between researchers seeking to strengthen Tor, or even develop a next generation anonymity tool, and governments around the world studying how to break Tor’s anonymity properties.
The most successful technique to de-anonymize Tor Browser users has been to hack them. The FBI has used this technique successfully in numerous criminal cases, and under Rule 41, enacted in 2016 by US Chief Justice Roberts of the Supreme Court, the FBI can now mass hack large numbers of computers anywhere in the world using a single warrant.
Such hacking techniques ought to concern everyone, as innocent Tor users will inevitably get caught up in such fishing expeditions.
Does that mean you shouldn’t use Tor? Certainly not, if you care about your privacy online. Tor Browser is an essential tool that will only improve with time. If you don’t care about your privacy? Well, Edward Snowden said it best:
Is Tor Browser legal?
For most people reading this article, Tor Browser is completely legal to use. In some countries, however, Tor is either illegal or blocked by national authorities. China has outlawed the anonymity service and blocks Tor traffic from crossing the Great Firewall. Countries such as Russia, Saudi Arabia and Iran, are working hard to prevent citizens from using Tor. Most recently, Venezuela has blocked all Tor traffic.
It’s easy to see why a repressive regime hates Tor. The service makes it easy for journalists to report on corruption and helps dissidents organize against political repression.
The freedom to communicate, publish, and read anonymously is a prerequisite for freedom of expression online, and thus a prerequisite for democracy today. Using and supporting Tor helps support freedom of expression around the world. Technically sophisticated users are encouraged to donate bandwidth to the Tor network by running a relay.













